Welcome
Getting Started
-
Quick Start
Concepts
-
Product Concepts
-
The FHIR Standard
- FHIR Introduction
- FHIR Versions
- FHIR CRUD Operations
- FHIR Searching Basics
- FHIR Search: References and Includes
- FHIR Search: Custom Search Parameters
- FHIR Search: Combo Search Parameters
- FHIR Search: Enforcing Uniqueness
- FHIR Search: Uplifted Refchains
- FHIR Transactions and Batches
- FHIRPath Expressions
- FHIRPath Patch
-
Testing Tools
Guides
-
Installing
- Platform Requirements
- Preparing a Linux Host
- Installing Smile CDR, NGINX and PostgreSQL in a Docker Stack
- Deploying a Kubernetes Managed Cluster
- Docker Container Installation
- Configuring Smile CDR
- Unix Service Installation
- Tuning your Installation
- Designing a Cluster
- Message Brokers
- Message Broker Failure Management
- Message Broker: Kafka
- Message Broker: ActiveMQ
- Message Broker: Pulsar
- Pre-Seeding Configuration and Data
- Production Checklist
- Module Licensing
-
Upgrading
-
Planning
-
Implementation
-
Tutorials
- Introduction
- Integration Testing Tutorial
- Custom Operations Tutorial
- HL7 v2.x Ingestion Tutorial
- Federated OAuth2/OIDC Tutorial
- MDM Tutorial
- MDM UI
- CDA Import Tutorial
- CDA Export Tutorial
- CDA Export - Custom Narrative Generation Tutorial
- CDA Import JSON example
- CDA Export Template JSON example
- Consent Tutorial
Reference
-
FHIR Storage
- FHIR Storage Modules
- FHIR Endpoint Module
- FHIRWeb Console
- OpenAPI / Swagger Support
- FHIR Endpoint Customization
- Resource IDs
- Search Parameters
- Search Parameter Features
- Phonetic Search Parameters
- Search Parameter Tuning
- Search Parameter Reindexing
- Searching for Data
- Creating Data
- Reading Data
- Updating Data
- Deleting Data
- Binary Data
- Externalized Resource Body Storage
- Working with Duplicates
- Request Tracing and Provenance
- Resource Versions and Versioned References
- Tags, Profiles, and Security Labels
- Partitioning and Multitenancy
- Custom Resource Types
- Batch and Scheduled Jobs
- Tokenization
- Bulk Resource Modification
-
FHIR Storage (MongoDB)
-
Validation and Conformance
- Introduction
- Validation Support Repository
- Validation Support Repository Options
- Conformance Data
- Repository Validation
- Repository Validation: Java
- Repository Validation: Javascript
- Repository Validation: Validation Bean
- Endpoint Validation
- Packages and Implementation Guides
- Package Registry Endpoint Module
- Remote Terminology Services
- Suppressing Messages
- Validation Performance
- Automatic Provenance Injection
-
Semantic Standardization
-
Interceptors
- Interceptors
- Pointcuts
- Starter Project
- Examples: FHIR Endpoints
- Examples: HL7v2 Endpoints
- Examples: FHIR Storage
- Examples: FHIR Gateway
- Examples: FHIR Client
- Examples: MDM
- Examples: Subscription
- Examples: Channel Import
- Examples: Cluster Manager
- Examples: App Sphere
- Examples: System To System Data Exchange
- 2024.02.01 Migration Guide
-
Channel Import
-
Security
- Authentication Protocols
- Authorization and Consent
- Inbound Security Module
- Local Inbound Security Module
- LDAP Inbound Security Module
- Scripted Inbound Security Module
- SAML Inbound Security Module
- Trusted Client Mode
- Roles and Permissions
- Callback Scripts
- Anonymous Access
- Consent Service
- Consent Service: JavaScript API
- Consent Service: Java API
- Security Recipes
- Two Factor Authentication
- Password Hashing Algorithms
- JWT Signature Algorithms
- Troubleshooting Security
-
Consent Module
-
SMART on FHIR
- SMART on FHIR: Introduction
- SMART: Scopes
- SMART: Auth Flows
- SMART: Endpoints
- SMART: Smile CDR Support
- SMART Outbound Security: Module
- SMART Outbound Security: Skinning
- SMART Outbound Security: Context Selection
- SMART Outbound Security: SAML Bridging
- SMART: Federated OAuth2/OIDC Login
- SMART: Application Approval/Consent
- SMART Inbound Security Module
- SMART Client Definitions
- SMART Server Definitions
- SMART OIDC Keystore Definitions
- SMART: Session Management
- SMART: Assigning Permissions
- SMART: Access Tokens
- SMART: User Profile Information
- FHIR Client Authentication
- SMART: Machine to Machine Authentication
-
FHIR Hybrid Providers
-
CDS Hooks
-
IG Support
-
HL7 v2.x Support
- Introduction
- Inbound Messaging
- FHIR-Based Terminology Translation
- Outbound Messaging
- Outbound: Default Resource Conversion
- Outbound: Custom Resource Conversion
- Outbound: Verbatim Messaging
- Outbound: Transport
- Transactions
- Structure Definitions
- Segment Definitions
- Table Definitions
- Naming System Mapping
- Processing Results Feeds
- Protocol
-
CDA Exchange+ Module
-
System to System Data Exchange
-
Bulk Operations
-
Additional Features
-
Product Administration
-
JSON Admin Endpoints
- JSON Admin API
- JSON Admin Home Endpoint
- MDM Endpoint
- Audit Log Endpoint
- Batch Job Endpoint
- Bulk Import Endpoint
- CDA Exchange Endpoint
- Config Diagnostics Endpoint
- Metrics Endpoint
- Module Config Endpoint
- OpenID Connect Clients Endpoint
- OpenID Connect Keystores Endpoint
- OpenID Connect Servers Endpoint
- OpenID Connect Sessions Endpoint
- Privacy Notice Endpoint
- Runtime Status Endpoint
- System Config Endpoint
- Transaction Log Endpoint
- Troubleshooting Log Endpoint
- User Management Endpoint
- Version Endpoint
-
HFQL: Direct SQL Access
-
Product Configuration
-
Java Execution Environment
-
JavaScript Execution Environment
- Introduction
- Specifying JavaScript in Configuration File
- Remote Debugging
- ECMA Modules (import)
- Converter API
- Environment API
- Exceptions API
- OAuth2 Exceptions API
- FHIR REST API
- FHIR Model API
- HL7 v2.x Mapping API
- HTTP API
- LDAP API
- Log API
- Composition Resource API
- Composition Section API
- TransactionBuilder API
- Util API
- UUID API
- XML API
- Callback Models
-
Localization
-
Smile CDR CLI (smileutil)
- Introduction
- Bulk Import
- Create FHIR Package
- Execute Script Function
- Export ConceptMap to CSV
- HL7 v2.x Analyze Flat File
- HL7 v2.x Transmit Flat File
- Import CSV to ConceptMap
- Map and Upload CSV Bulk Import File
- Migrate Database
- Clear Database Migration Lock
- Module Config Properties Export
- Reindex Terminology
- Synchronize FHIR Servers
- Upgrade H2 Database File
- Upload Bundle Files
- Upload CSV Bulk Import File
- Upload Sample Dataset
- Upload Terminology
- Generate Realtime Export Schema
- Validate FHIR Resources
-
Apache Camel Integration
- Camel Module Overview
- Smile Camel Processors
- Processors: FHIR Storage module
- Processors: ETL Import module
- Processors: Camel module
- Processors: Cluster Manager module
- Processors: HL7v2 Inbound module
- Processors: CDA Exchange+ module
- Processors: Semantic Standardization module
- Processors: Transaction Logging
- Smile Camel Converters
- Smile Camel Recipes
-
Prior Auth CRD (Coverage Requirement Discovery)
-
Prior Auth DTR (Documentation Templates and Rules)
-
Prior Auth Support
-
Smile Portal
-
Davinci Data Exchange
-
Modules
- JSON Admin API
- Web Admin Console
- CDA Exchange+
- CDA Exchange(Deprecated)
- Channel Import
- Cluster Manager
- CQL
- Audit Log Persistence
- Audit Log OpenTelemetry
- Transaction Log Persistence
- Transaction Log OpenTelemetry
- Digital Quality Measures (DQM)
- Documentation Templates and Rules (DTR)
- Enterprise Master Patient Index
- CDS Hooks Endpoint
- FHIR Gateway Endpoint
- FHIR REST Endpoint (All Versions)
- FHIR REST Endpoint (DSTU2 - Deprecated)
- FHIR REST Endpoint (DSTU3 - Deprecated)
- FHIR REST Endpoint (R4 - Deprecated)
- FHIRWeb Console
- HL7 v2.x Listening Endpoint
- HL7 v2.x Listening Endpoint (Deprecated)
- HL7 v2.x Sending Endpoint
- Hybrid Providers Endpoint
- Package Registry Endpoint
- Subscription Websocket Endpoint
- ETL Importer
- MDM
- MDM UI
- Prior Auth CRD
- Prior Auth Support
- Narrative Generator
- FHIR Storage (DSTU2 RDBMS)
- FHIR Storage (R3 RDBMS)
- FHIR Storage (R4 RDBMS)
- FHIR Storage (R5 RDBMS)
- FHIR Storage (Mongo)
- Realtime Export
- LDAP Inbound Security
- Local Inbound Security
- SAML Inbound Security
- Scripted Inbound Security
- SMART Inbound Security
- SMART Outbound Security
- Subscription Matcher (All FHIR Versions)
- Subscription Matcher (DSTU2 - Deprecated)
- Subscription Matcher (DSTU3 - Deprecated)
- Subscription Matcher (R4 - Deprecated)
- appSphere
- Payer to Payer (Deprecated)
- System to System Data Exchange
- License
- Camel
- Consent Module
- Smile Portal
- Davinci Data Exchange
-
Appendix
Generated Reference
-
Configuration Categories
- Web Admin Console Settings
- appSphere
- Payer Config
- Initial appSphere Seeding
- Authentication Callback Scripts
- Auth: General for APIs
- User Authentication
- Auth: HTTP Basic
- Auth: OpenID Connect
- Browser Syntax Highlighting
- Camel
- Capability Statement (metadata)
- Care Gaps
- CDA Export
- CDA Import
- CDA Interceptors
- CDA JavaScript Execution Scripts
- CDA Terminology
- CDS Hooks Definitions
- CDS Hooks On FHIR
- Channel Import
- Channel Retry
- Cluster Manager Interceptors
- Kafka
- Cluster Manager Maintenance
- Message Broker
- Pulsar
- Cluster Level Security
- Consent
- CQL
- Credentials
- Cross-Origin Resource Sharing (CORS)
- Invoke Export
- Member Match
- Database
- Da Vinci Health Record Exchange
- EasyShare SMART Health Links
- Email Configuration
- MDM UI
- ETL Import: CSV Properties
- ETL Import: Source
- Measure Evaluation
- External Object Storage
- FHIR Binary Storage
- FHIR Bulk Modification Operations
- FHIR Bulk Import/Export Operations
- Capability Statement
- FHIR Configuration
- Consent Service
- FHIR Endpoint Conversion
- FHIR Endpoint HFQL Support
- FHIR Endpoint Partitioning
- Resource Providers
- FHIR Endpoint Security
- Endpoint Terminology
- FHIR Gateway Cache
- FHIR Gateway Configuration
- FHIR Interceptors
- LiveBundle Service
- FHIR MDM Server
- FHIR Performance
- FHIR Performance Tracing
- FHIR Realtime Export
- Repository Validation
- FHIR Resource Body Storage
- FHIR Resource Types
- FHIR REST Endpoint
- FHIR Search
- Custom Resource Types
- IG Support
- MegaScale
- FHIR Storage Module Conditional Updates
- FHIR Storage Module Scheduled Tasks
- FHIR Validation Services
- FHIR Validation Services Remote Terminology Client TLS / SSL (Encryption)
- FHIR Storage Package Registry
- FHIR Storage Partitioning
- Versioned References
- FHIR Subscription Delivery
- FHIR Subscription Persistence
- FHIR Tokenization
- Full-Text Indexing
- HL7 v2.x Mapper - Contained Resource
- HL7 v2.x Mapper - DG1
- HL7 v2.x Mapper - Forced Namespace Mode
- HL7 v2.x Mapper - General
- HL7 v2.x Mapper - Medications
- HL7 v2.x Mapper - OBR
- HL7 v2.x to FHIR Mapper - OBSERVATION Group
- HL7 v2.x Mapper - ORC
- HL7 v2.x to FHIR Mapper - ORDER_OBSERVATION Group
- HL7 v2.x Mapper - PID
- HL7 v2.x Mapper - PV1
- HL7 v2.x Mapper - TXA
- Listener Interceptors
- HL7 v2.x Listener Script
- HL7 v2.x Listening Endpoint
- HL7 v2.x MLLP Listener
- HL7 v2.x MLLP Sender
- FHIR to HL7 v2.x Mapper Script
- HL7 v2.x Outbound Mapping
- HTTP Access Log
- HTTP Listener
- HTTP Request Pool
- HTTP Security
- Hybrid Providers Definitions
- IG Support
- Initial Custom Roles Seeding
- Initial User Seeding
- JavaScript Execution Environment
- JSON Web KeySet (JWKS)
- LDAP Authentication
- Smile CDR License
- MDM
- Migration
- Narrative Generator
- OpenID Connect Token Validation
- OpenID Connect (OIDC)
- Prior Authorization Coverage Requirement Discovery
- Prior Authorization Documentation Templates and Requirements
- Prior Authorization Support
- Privacy Security Notice
- Provenance Injection
- Quality Payment Program (QPP)
- Realtime Export
- Endpoint Validation: Request Validating
- Search Parameter Seeding
- SAML Provider
- Security Inbound Script
- Inbound SMART on FHIR Authentication
- Inbound SMART on FHIR Endpoints
- OAuth2/OIDC Federation
- SMART Callback Script
- Cross-Organizational Data Access Profile
- SMART Login Skin
- SMART Login Terms of Service
- SMART Authorization
- SMART Definitions Seeding
- Semantic Standardization Configuration
- Sessions
- Smile Portal
- Two Factor Authentication
- TLS / SSL (Encryption)
- Transaction Log
- Trusted Client
- User Self Registration
- Web Admin Console Settings
- appSphere
- Payer Config
- Initial appSphere Seeding
- Authentication Callback Scripts
- Auth: General for APIs
- User Authentication
- Auth: HTTP Basic
- Auth: OpenID Connect
- Browser Syntax Highlighting
- Camel
- Capability Statement (metadata)
- Care Gaps
- CDA Export
- CDA Import
- CDA Interceptors
- CDA JavaScript Execution Scripts
- CDA Terminology
- CDS Hooks Definitions
- CDS Hooks On FHIR
- Channel Import
- Channel Retry
- Cluster Manager Interceptors
- Kafka
- Cluster Manager Maintenance
- Message Broker
- Pulsar
- Cluster Level Security
- Consent
- CQL
- Credentials
- Cross-Origin Resource Sharing (CORS)
- Invoke Export
- Member Match
- Database
- Da Vinci Health Record Exchange
- EasyShare SMART Health Links
- Email Configuration
- MDM UI
- ETL Import: CSV Properties
- ETL Import: Source
- Measure Evaluation
- External Object Storage
- FHIR Binary Storage
- FHIR Bulk Modification Operations
- FHIR Bulk Import/Export Operations
- Capability Statement
- FHIR Configuration
- Consent Service
- FHIR Endpoint Conversion
- FHIR Endpoint HFQL Support
- FHIR Endpoint Partitioning
- Resource Providers
- FHIR Endpoint Security
- Endpoint Terminology
- FHIR Gateway Cache
- FHIR Gateway Configuration
- FHIR Interceptors
- LiveBundle Service
- FHIR MDM Server
- FHIR Performance
- FHIR Performance Tracing
- FHIR Realtime Export
- Repository Validation
- FHIR Resource Body Storage
- FHIR Resource Types
- FHIR REST Endpoint
- FHIR Search
- Custom Resource Types
- IG Support
- MegaScale
- FHIR Storage Module Conditional Updates
- FHIR Storage Module Scheduled Tasks
- FHIR Validation Services
- FHIR Validation Services Remote Terminology Client TLS / SSL (Encryption)
- FHIR Storage Package Registry
- FHIR Storage Partitioning
- Versioned References
- FHIR Subscription Delivery
- FHIR Subscription Persistence
- FHIR Tokenization
- Full-Text Indexing
- HL7 v2.x Mapper - Contained Resource
- HL7 v2.x Mapper - DG1
- HL7 v2.x Mapper - Forced Namespace Mode
- HL7 v2.x Mapper - General
- HL7 v2.x Mapper - Medications
- HL7 v2.x Mapper - OBR
- HL7 v2.x to FHIR Mapper - OBSERVATION Group
- HL7 v2.x Mapper - ORC
- HL7 v2.x to FHIR Mapper - ORDER_OBSERVATION Group
- HL7 v2.x Mapper - PID
- HL7 v2.x Mapper - PV1
- HL7 v2.x Mapper - TXA
- Listener Interceptors
- HL7 v2.x Listener Script
- HL7 v2.x Listening Endpoint
- HL7 v2.x MLLP Listener
- HL7 v2.x MLLP Sender
- FHIR to HL7 v2.x Mapper Script
- HL7 v2.x Outbound Mapping
- HTTP Access Log
- HTTP Listener
- HTTP Request Pool
- HTTP Security
- Hybrid Providers Definitions
- IG Support
- Initial Custom Roles Seeding
- Initial User Seeding
- JavaScript Execution Environment
- JSON Web KeySet (JWKS)
- LDAP Authentication
- Smile CDR License
- MDM
- Migration
- Narrative Generator
- OpenID Connect Token Validation
- OpenID Connect (OIDC)
- Prior Authorization Coverage Requirement Discovery
- Prior Authorization Documentation Templates and Requirements
- Prior Authorization Support
- Privacy Security Notice
- Provenance Injection
- Quality Payment Program (QPP)
- Realtime Export
- Endpoint Validation: Request Validating
- Search Parameter Seeding
- SAML Provider
- Security Inbound Script
- Inbound SMART on FHIR Authentication
- Inbound SMART on FHIR Endpoints
- OAuth2/OIDC Federation
- SMART Callback Script
- Cross-Organizational Data Access Profile
- SMART Login Skin
- SMART Login Terms of Service
- SMART Authorization
- SMART Definitions Seeding
- Semantic Standardization Configuration
- Sessions
- Smile Portal
- Two Factor Authentication
- TLS / SSL (Encryption)
- Transaction Log
- Trusted Client
- User Self Registration
-
Module Dependencies
-
Product Reference
-
Tags
- Pages tagged with "activemq"
- Pages tagged with "admin-json"
- Pages tagged with "admin-ui"
- Pages tagged with "advanced"
- Pages tagged with "api"
- Pages tagged with "app-gallery"
- Pages tagged with "architecture"
- Pages tagged with "audit"
- Pages tagged with "authentication"
- Pages tagged with "authorization"
- Pages tagged with "automation"
- Pages tagged with "aws"
- Pages tagged with "azure"
- Pages tagged with "batch-operations"
- Pages tagged with "batch-processing"
- Pages tagged with "beginner"
- Pages tagged with "best-practices"
- Pages tagged with "bulk-operations"
- Pages tagged with "caching"
- Pages tagged with "camel"
- Pages tagged with "care-gaps"
- Pages tagged with "cda"
- Pages tagged with "cda-exchange-plus"
- Pages tagged with "cds"
- Pages tagged with "cds-hooks"
- Pages tagged with "certification"
- Pages tagged with "changelog"
- Pages tagged with "channel-import"
- Pages tagged with "clinical-reasoning"
- Pages tagged with "cloud"
- Pages tagged with "cluster"
- Pages tagged with "codesystem"
- Pages tagged with "compliance"
- Pages tagged with "composition"
- Pages tagged with "concept"
- Pages tagged with "conceptmap"
- Pages tagged with "configuration"
- Pages tagged with "conformance"
- Pages tagged with "consent"
- Pages tagged with "conversion"
- Pages tagged with "cql"
- Pages tagged with "csv"
- Pages tagged with "customization"
- Pages tagged with "da-vinci"
- Pages tagged with "database"
- Pages tagged with "davinci"
- Pages tagged with "debugging"
- Pages tagged with "dependencies"
- Pages tagged with "deployment"
- Pages tagged with "deprecated"
- Pages tagged with "developer"
- Pages tagged with "diagnostics"
- Pages tagged with "docker"
- Pages tagged with "document-generation"
- Pages tagged with "documentation"
- Pages tagged with "dqm"
- Pages tagged with "easyshare"
- Pages tagged with "elasticsearch"
- Pages tagged with "error-handling"
- Pages tagged with "etl"
- Pages tagged with "etl-import"
- Pages tagged with "experimental"
- Pages tagged with "export"
- Pages tagged with "feature-maturity"
- Pages tagged with "features"
- Pages tagged with "fhir"
- Pages tagged with "fhir-client"
- Pages tagged with "fhir-endpoint"
- Pages tagged with "fhir-gateway"
- Pages tagged with "fhir-repository"
- Pages tagged with "fhir-storage"
- Pages tagged with "fhirpath"
- Pages tagged with "getting-started"
- Pages tagged with "grafana"
- Pages tagged with "guide"
- Pages tagged with "health-checks"
- Pages tagged with "hl7v2"
- Pages tagged with "how-to"
- Pages tagged with "howto"
- Pages tagged with "http"
- Pages tagged with "hybrid-providers"
- Pages tagged with "indexing"
- Pages tagged with "ingestion"
- Pages tagged with "integration"
- Pages tagged with "interceptors"
- Pages tagged with "intermediate"
- Pages tagged with "internationalization"
- Pages tagged with "interoperability"
- Pages tagged with "java"
- Pages tagged with "javascript"
- Pages tagged with "jdbc"
- Pages tagged with "junit"
- Pages tagged with "jvm"
- Pages tagged with "jwt"
- Pages tagged with "kafka"
- Pages tagged with "kubernetes"
- Pages tagged with "ldap"
- Pages tagged with "libraries"
- Pages tagged with "licensing"
- Pages tagged with "linux"
- Pages tagged with "logging"
- Pages tagged with "logs"
- Pages tagged with "loinc"
- Pages tagged with "mappings"
- Pages tagged with "mariadb"
- Pages tagged with "mdm"
- Pages tagged with "member-match"
- Pages tagged with "message-broker"
- Pages tagged with "messaging"
- Pages tagged with "metrics"
- Pages tagged with "migration"
- Pages tagged with "module-management"
- Pages tagged with "mongodb"
- Pages tagged with "monitoring"
- Pages tagged with "mssql"
- Pages tagged with "mysql"
- Pages tagged with "narrative"
- Pages tagged with "navigation"
- Pages tagged with "ndjson"
- Pages tagged with "nginx"
- Pages tagged with "oauth2"
- Pages tagged with "observability"
- Pages tagged with "openid"
- Pages tagged with "opentelemetry"
- Pages tagged with "operations"
- Pages tagged with "oracle"
- Pages tagged with "otel"
- Pages tagged with "overview"
- Pages tagged with "packages"
- Pages tagged with "partitioning"
- Pages tagged with "patient"
- Pages tagged with "patient-matching"
- Pages tagged with "payer-to-payer"
- Pages tagged with "performance"
- Pages tagged with "permissions"
- Pages tagged with "postgresql"
- Pages tagged with "premium"
- Pages tagged with "privacy"
- Pages tagged with "processors"
- Pages tagged with "product-administration"
- Pages tagged with "product-lifecycle"
- Pages tagged with "product-planning"
- Pages tagged with "production"
- Pages tagged with "prometheus"
- Pages tagged with "provenance"
- Pages tagged with "pulsar"
- Pages tagged with "quality-measures"
- Pages tagged with "redis"
- Pages tagged with "reference"
- Pages tagged with "releases"
- Pages tagged with "remote-services"
- Pages tagged with "repository"
- Pages tagged with "rest-api"
- Pages tagged with "roadmap"
- Pages tagged with "saml"
- Pages tagged with "scripting"
- Pages tagged with "sdc"
- Pages tagged with "search"
- Pages tagged with "security"
- Pages tagged with "semantic-standardization"
- Pages tagged with "session-management"
- Pages tagged with "smart"
- Pages tagged with "snomed"
- Pages tagged with "spring-batch"
- Pages tagged with "sql"
- Pages tagged with "storage"
- Pages tagged with "structuredefinition"
- Pages tagged with "subscription"
- Pages tagged with "swagger"
- Pages tagged with "system-to-system-data-exchange"
- Pages tagged with "systemd"
- Pages tagged with "templates"
- Pages tagged with "terminology"
- Pages tagged with "testcontainers"
- Pages tagged with "testing"
- Pages tagged with "tls"
- Pages tagged with "transaction-logging"
- Pages tagged with "transactions"
- Pages tagged with "transformation"
- Pages tagged with "translation"
- Pages tagged with "troubleshooting"
- Pages tagged with "tutorial"
- Pages tagged with "upgrading"
- Pages tagged with "user-management"
- Pages tagged with "validation"
- Pages tagged with "valueset"
- Pages tagged with "version-info"
- Pages tagged with "versioning"
- Pages tagged with "web-ui"
- Pages tagged with "websocket"
- Pages tagged with "xml"
Getting Started
27.1.1Getting StartedTrial
Assuming that users have already installed SmileCDR, the following steps describe how a customer can begin to use appSphere.
-
Log in to the Smile CDR Web Admin Console (the administration UI for configuring the system).
-
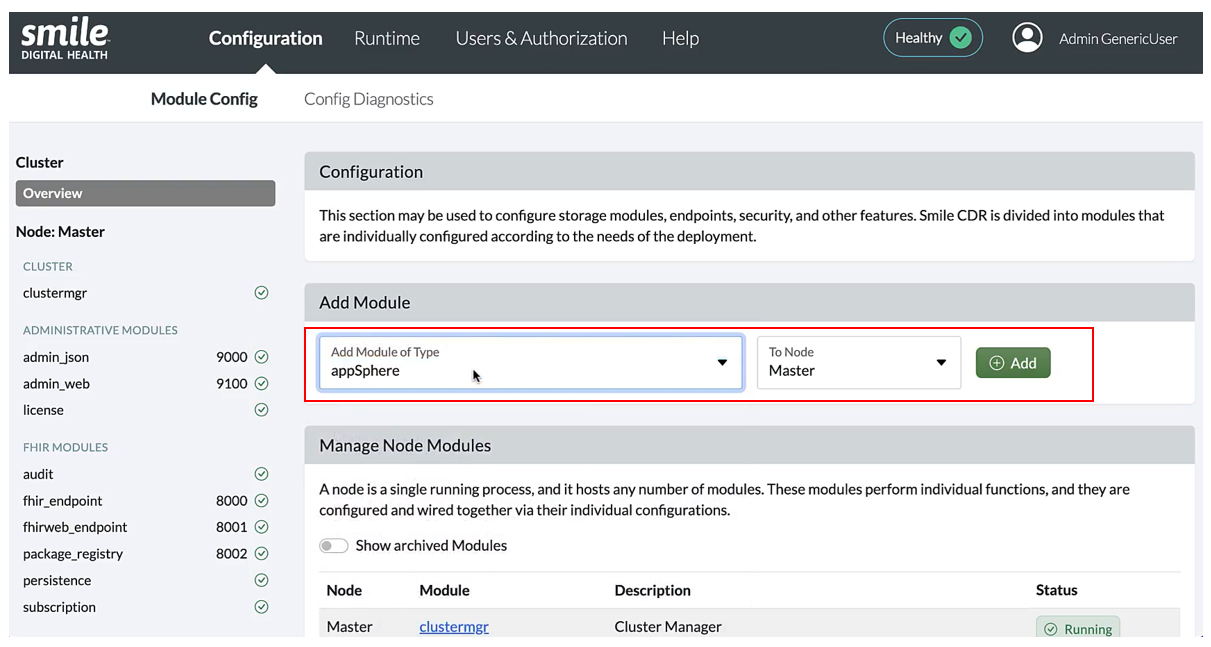
Create a new appSphere module by going to the “Manage Node Modules” section, selecting “appSphere” from the “Add Module of Type” drop-down list, then clicking “Add”.
The following page will open after clicking "Add" which allows the user to enter additional any configurations.
** IMPORTANT NOTE **
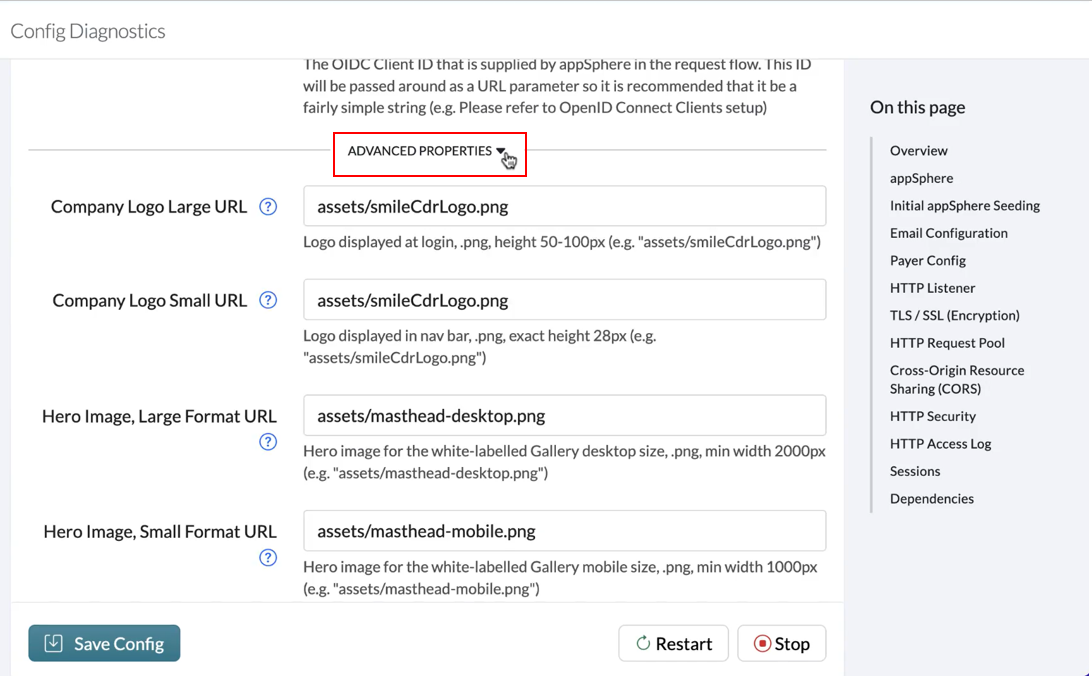
After a module has been created, “Default” configuration mode will be visible to users. To view “Advanced” configuration mode, check the box provided at the top right corner of the module page.
"Advanced Config" include fields such as Company Logo Small URL and Company Logo Large URL , for the location of the logo you’d like to show on appSphere's login page and navigation bar. Smile CDR’s logo is a placeholder by default.
Appropriate domain and context path should be used to configure the URLs. There are examples of the URLs for each field.
** IMPORTANT NOTE **
The Auth URL, FHIR URL, and JSON URL must match those used in the respective modules. Similarly, the ** Client ID** name used in this section must match the name of the OpenID Connect Client that needs to be created, which is described under the Client Creation and Configuration section. The names of each of the components can also be changed to suit your preferences. In addition, the parent page for the link provided for the PHI Warning URL can be found here.
In the Initial appSphere Seedingsection, the Attestation Title and HTML file for both the legal and plain version are already added by default for the first version.
In the Email Configuration section, ensure the following configurations are made (detailed steps are available here) to enable developers to get notified if the status of their app changes, or if a new attestation version is created that requires them to re-attest:
- Email From Address: (e.g., name@yourcompany.com)
- Notification Emails: (Console Managers will use these emails to receive notifications for new registrations and document uploads)
Ensure that the necessary details are provided for the following fields as described below:
- In the
Listener Portfield, enter an appropriate port number (e.g., 19300). - In the
Context Pathfield, enter a name you’d like to use for the URL path (e.g., /app-gallery/). - Toggle
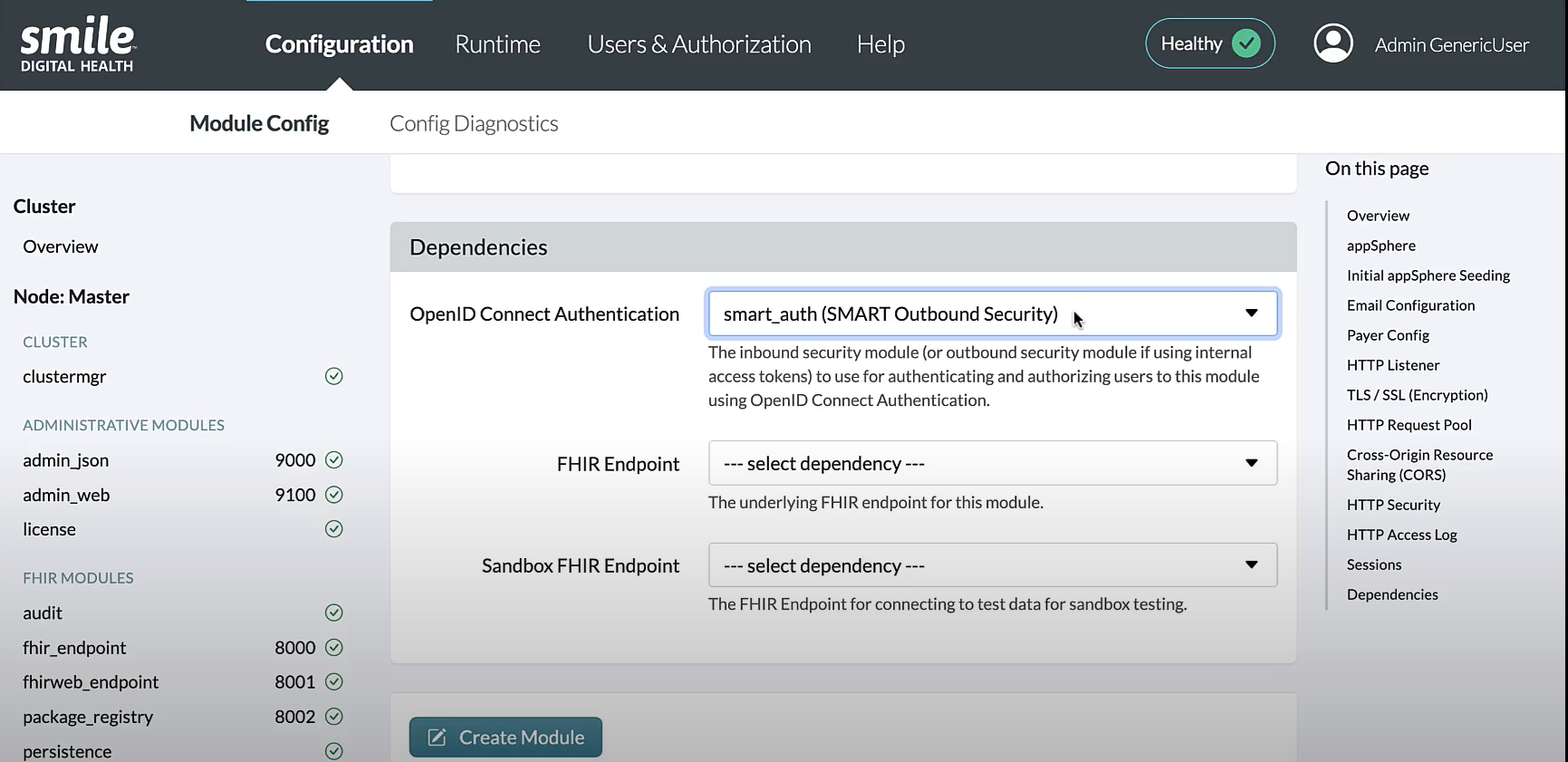
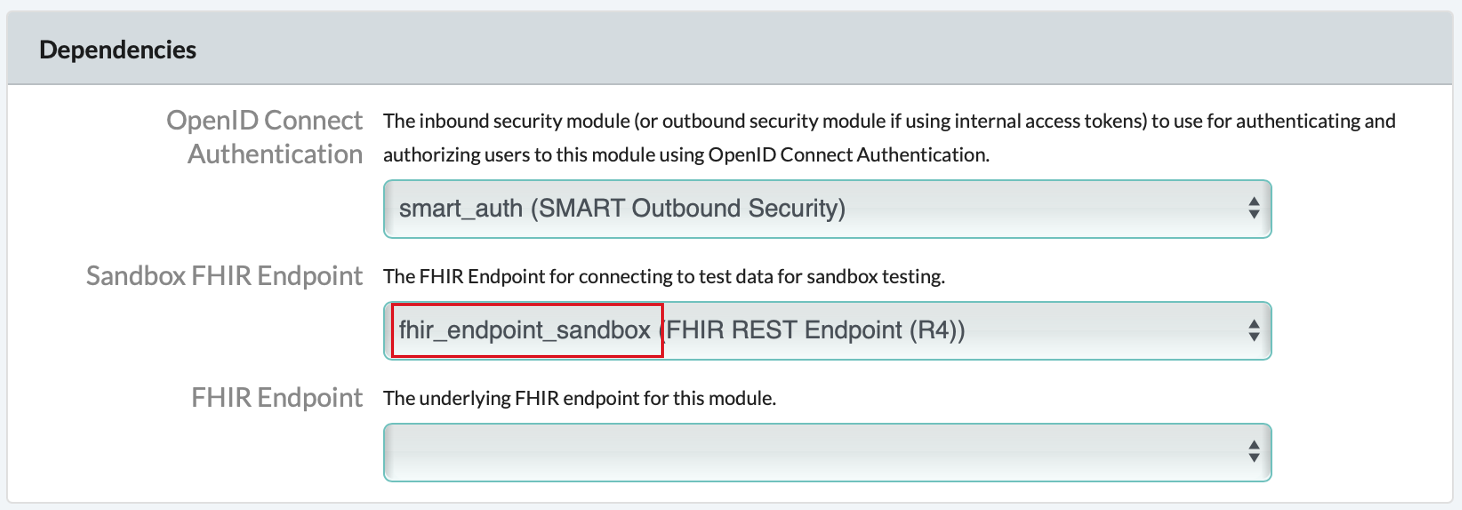
Respect Forward HeadersandCORS EnabledtoYes - Under the Dependencies section, for the OpenID Connect Authentication dropdown, select the SMART Outbound Security
module that matches the value in the
Auth URLfield, e.g.,smart_auth (SMART Outbound Security).
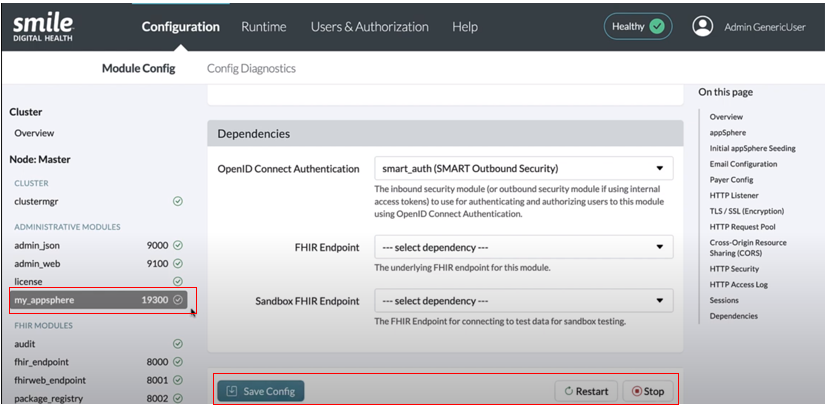
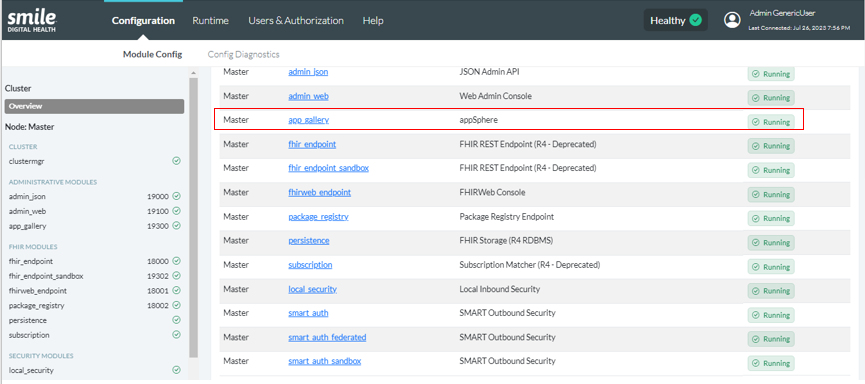
After entering the necessary details, click “Save”. On the "Module Config" page, you should see appSphere added to the list of modules in the Master node, under the Administrative Modules section in the menu pane on the left. It is recommended to “Restart” the module if any changes are made. A green checkmark icon indicates a correctly functioning module.
The appSphere module can then be selected from the list of modules listed under “Manage Node Module” on the "Config" page to make changes in the configurations, save the changes made, and archive them.
27.1.2Setting-up a Sandbox EnvironmentTrial
To set up a sandbox environment for developers to test their apps, the following steps need to be followed:
- Create a new SMART Outbound Security module
- Create a new FHIR REST Endpoint (R4) module
- Add the relevant FHIR Sandbox URL and Sandbox FHIR Endpoint dependencies in the appSphere module configuration
- Ensure that developer accounts have the correct permissions
Create a new smart_auth (SMART Outbound Security) module called smart_auth_sandbox. Full configuration for the smart_auth module is described here. However, ensure the following changes are made so that the smart_auth_sandbox module is distinguishable from the already configured smart_auth (SMART Outbound Security) module:
- Module ID: smart_auth_sandbox
- Listener Port: an open port (e.g., 19301)
- Context Path: /auth-sandbox/
- Issuer URL: [your-domain]/auth-sandbox
- Username/Password Authentication: local_security (Local Inbound Security)
After the configurations have been made, select “Save” at the top of the page to get redirected to the “Configuration” page. A confirmation message would be displayed for the newly added module. It is recommended to “Restart” the module if any changes are made.
On the same page, the newly added module will be displayed under the “Manage Node Modules” table and in the Security Modules section in the menu pane on the left with a green checkmark icon to indicate a correctly functioning module.
Create a new fhir_endpoint (FHIR REST Endpoint R4) module called fhir_endpoint_sandbox. Full configuration for the fhir_endpoint module is described here. However, ensure the following changes are made so that the fhir_endpoint_sandbox module is distinguishable from the other fhir_endpoint module:
- Module ID: fhir_endpoint_sandbox
- Listener Port: an open port (e.g., 19302)
- Context Path: /fhir-sandbox/
- Username/Password Authentication: local_security (Local Inbound Security)
- OpenID Connect Authentication: smart_auth_sandbox (SMART Outbound Security)
After the configurations have been made, select “Save” at the top of the page to get redirected to the “Configuration” page. A confirmation message would be displayed for the newly added module. It is recommended to “Restart” the module if any changes are made.
On the same page, the newly added module will be displayed under the “Manage Node Modules” table and in the FHIR Modules section in the menu pane on the left with a green checkmark icon to indicate a correctly functioning module.
In the appSphere module, ensure that the following are assigned:
- FHIR Sandbox URL:
[your-domain]/fhir-sandbox(URL of FHIR Endpoint configured above) - Sandbox FHIR Endpoint (under the Dependencies section):
fhir_endpoint_sandbox (FHIR REST Endpoint (R4))
** IMPORTANT NOTE **
Ensure that fhir_endpoint_sandbox (FHIR REST Endpoint (R4)) is using a different OpenID Connect Authentication dependency than that of appSphere (or appSphere's FHIR Endpoint dependency, if provided), to ensure that only test data can be accessed during sandbox testing.
After the configurations have been made, select “Save” at the top of the page to get redirected to the “Configuration” page. It is recommended to “Restart” the module if any changes are made.
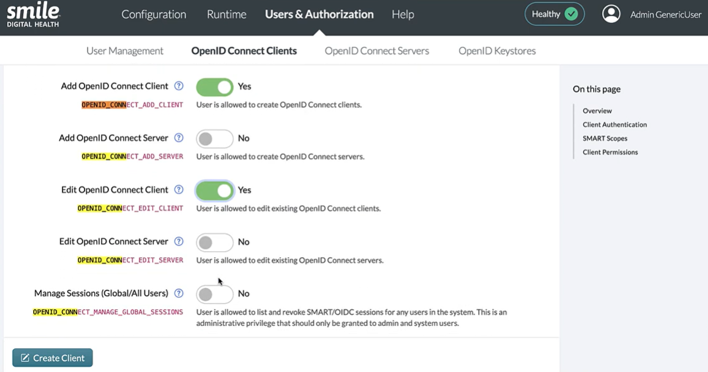
** IMPORTANT NOTE **
In order to ensure developers can access the sandbox feature, ensure that the OPENID_CONNECT_ADD_CLIENT
and OPENID_CONNECT_EDIT_CLIENT permissions are granted.
See here to learn how to grant the required permission.
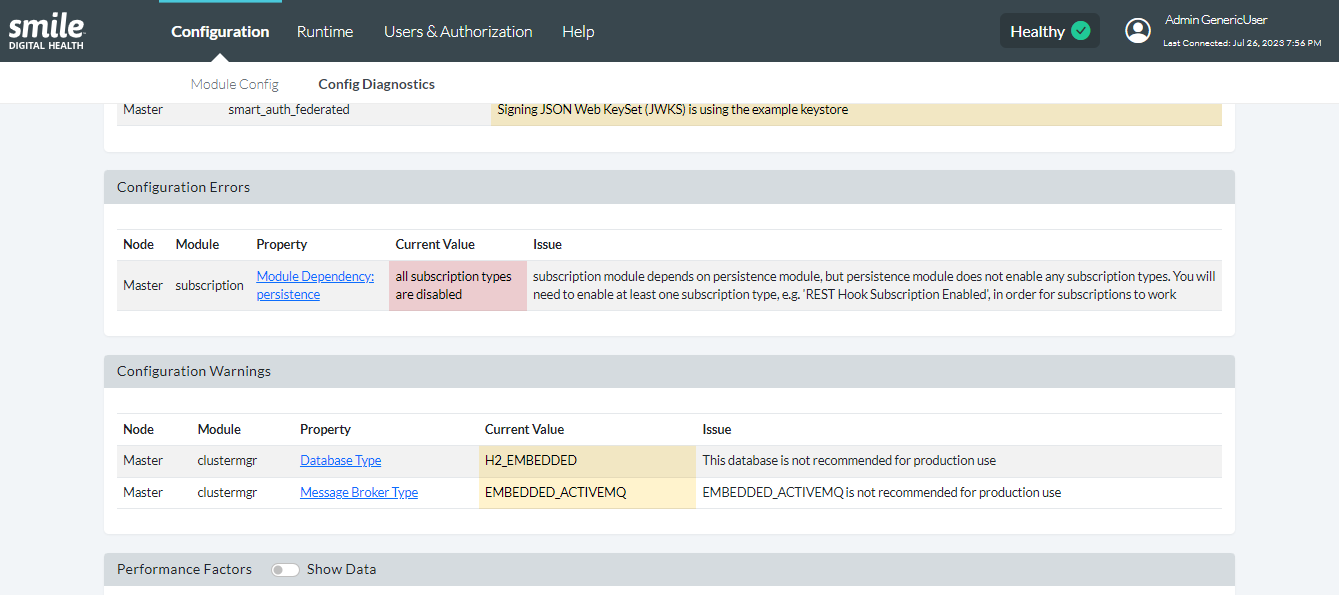
27.1.3Config DiagnosticsTrial
On the landing page of Smile CDR Web Admin Console, the “Config Diagnostics” page is also available in the drop-down list under “Config” on the header's navigation menu.
The “Config Diagnostics” page provides a summary of warnings and errors in relation to the configurations made to set up all modules, including appSphere. A warning is meant to show configurations that would lead to an issue. An error shows issues caused as a result of incorrect configurations. The issue column provides recommendations on how the warnings or errors should be addressed (more information can be found here).